Yisda Insights: Cybersecurity Threats in Critical Infrastructure
- Yisda Technical Team

- Jan 13
- 3 min read
Updated: Feb 10
Understanding the Risks of Credential Theft and Malware Deployment
Across these cases, initial access through VPNs and phishing quickly translated into credential theft, malware deployment, and even hypervisor-level risk. This underscores the value of zero trust access and micro-segmentation to limit lateral movement after a foothold is gained.
This week’s newsletter looks at how routine entry points and familiar user interactions are being chained into outsized compromises. Huntress described a suspected China-linked operation where access via a compromised SonicWall VPN appliance preceded deployment of a multi-part VMware ESXi virtual machine escape toolkit. This toolkit can lead to control at the hypervisor layer. Recorded Future’s Insikt Group tied multiple 2025 credential-harvesting efforts to APT28, showing how tailored phishing and easily swapped infrastructure can collect logins while sending victims back to legitimate destinations to avoid detection. CloudSEK also linked MuddyWater to RustyWater delivery via spear phishing across Middle East sectors, consistent with the group’s movement away from off-the-shelf remote access tools and toward custom implants. Together, these cases highlight adversaries blending reliable access paths, low-noise tactics, and purpose-built tooling.

Suspected China-Linked Toolkit Turns SonicWall VPN Breach Into ESXi Hypervisor Control
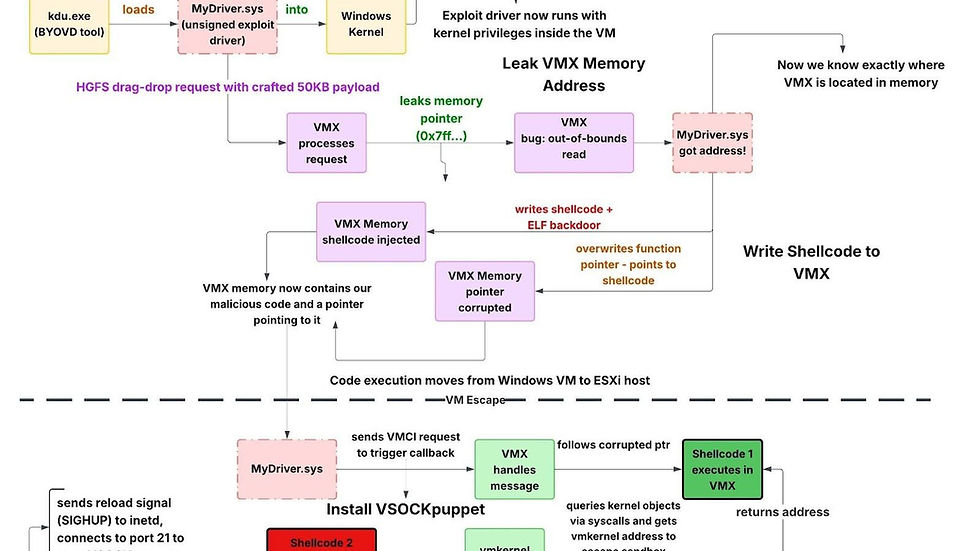
Huntress observed activity where threat actors used a compromised SonicWall VPN appliance as the initial access vector. This led to the deployment of a multi-component VMware ESXi virtual machine escape toolkit. The attack chain abuses three VMware vulnerabilities disclosed as zero-day issues in March 2025. It can culminate in hypervisor-level control from inside a guest virtual machine. Huntress cited simplified Chinese strings in development paths and the sophistication of the chain as indicators that the toolkit likely originated from a well-resourced developer operating in a Chinese-speaking region. It may be distributed selectively through private channels.
APT28 Uses Tailored Phishing and Disposable Hosting to Harvest Credentials
Recorded Future’s Insikt Group attributed several 2025 credential-harvesting campaigns to APT28, also known as BlueDelta. They targeted a small set of individuals tied to a Turkish energy and nuclear research agency, a European think tank, and organizations in North Macedonia and Uzbekistan. The lures use shortened links and a staged redirect chain. This briefly displays a legitimate PDF lure before sending victims to look-alike sign-in pages for services such as Microsoft Outlook Web Access, Google, and Sophos VPN portals. The phishing pages use embedded scripts and forms to signal page opens, capture submitted credentials, and then redirect victims back to legitimate sites. They rely on disposable hosting and relay services that are easy to rotate.
MuddyWater Delivers RustyWater RAT via Spear-Phishing in the Middle East
CloudSEK attributed a Middle East spear-phishing campaign against diplomatic, maritime, financial, and telecom entities to MuddyWater. Researchers assess this group is affiliated with Iran’s Ministry of Intelligence and Security. The emails masquerade as cybersecurity guidance and deliver a malicious Word document. Enabling content triggers a VBA macro that deploys a Rust implant tracked as RustyWater, Archer RAT, and RUSTRIC. The malware gathers victim machine information, checks installed security software, persists via a Windows Registry key, and connects to nomercys.it to support command execution and file operations. The report framed this as part of MuddyWater’s shift away from legitimate remote access tooling toward custom malware. Seqrite Labs recently reported RUSTRIC in Israel-targeted attacks.

Yisda Takeaways
This week’s newsletter highlights how attackers are chaining ordinary access paths into outsized outcomes across virtualization, identity, and endpoint tradecraft. The Huntress reporting underscores how perimeter devices like VPN appliances can still provide a viable path into environments running ESXi. Hypervisor escape toolkits raise the stakes by enabling control at the virtualization layer once an attacker is inside.
The APT28 campaigns reinforce that credential harvesting remains a reliable and low-friction tactic. This is especially true when paired with disposable hosting, redirect chains, and believable lures that return victims to legitimate sites to reduce suspicion. The MuddyWater activity shows continued investment in custom implants. RustyWater is delivered through familiar spear-phishing workflows and designed for persistence and post-compromise control.
These developments suggest a clear set of priorities: reduce external attack surface and harden remote access. Limit lateral movement through segmentation and strong identity controls. Strengthen detection and user readiness around phishing and document-based execution. This is crucial so initial footholds do not escalate into full environment compromise.
Conclusion
The landscape of cyber threats is evolving. As critical infrastructure operators, we must remain vigilant. Understanding these tactics is essential. We need to adapt our defenses accordingly. By implementing robust security measures, we can protect our essential services. The stakes have never been higher. Let's act decisively to safeguard our systems.
---wix---



Comments